







Android is most popular operative system for mobile devices in current time. It exist because open code of Android give huge opportunities for manufacturer of software to create special applications. So Android give opportunity to get Root right for customer, that means everyone can create own application and install it into own device.
However lot of opportunities could be source of troubles for customer, because application may be threat for safety of customer`s personal data. Malware installed into your device can send your personal information, such your e-mails, passwords, photos, documents, routs and etc. in cyber criminal`s hands.
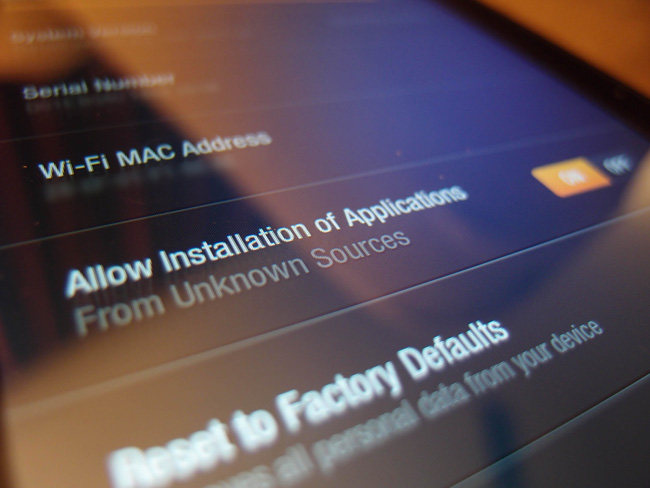
Creators of Android and big team of engineers develop improvements of it every day to make Android more safe and don`t introversion of open code what was the best idea at first steps of Android life. So official shop of application Google Play constantly inspect offered software for potential threats. But customer can install application from unknown source by switch accordance menu button off.
In most cases viruses and malware infiltrate to your device together with application from dishonest manufacturer. You must be carefully to input your phone number in forms of raise a doubt sites. Also be carefully to jump by received links from unknown senders. This movement can bring many problems to your Android and you as well.
Malicious hackers make malware application every day, but their work by few similar scenarios. Below you can read main description of every type.
This type of virus is one of oldest, but popular enough among hackers. Main task of Trojan is collect personal information about user and send it to creator of virus. In last time this malware began to hack mobile bank application to get access to your bank account.
Receiving of Root rights at Android need specific know ledges and skills therefore developers begin to release applications for easier this process. But cyber criminals also began to use this trend. In result they get possibility to full run of your gadget included installation of external soft, reading of codes, passwords and other data.
Sometime this type of virus has been very popular among malicious hacker. Soon after installation malware send short message to chargeable short numbers. Also malware can subscribe you to any chargeable service and fee for that debited from customer`s balance.
Application listened, recorded and transferred every phone conversation of user directed to fond and save confidential and private information about customer. This information hacker can use in future or to sell it to another concerned person or group.
Viruses and malwares to leak in Android through application from unknown Internet recourses or by jump to unknown links. So, in most cases user give permission to install it itself. Most effective method to defend your Android-gadget is rejection to install application from unknown resources.
Be carefully when you choose resource of downloading needed applications. When possible to use download only from official source of the manufacturer or Google Play.






